Description
Numerous modern solutions exist for securely connecting Linux systems behind NAT. However, many of these solutions rely on external libraries and specific programming languages.
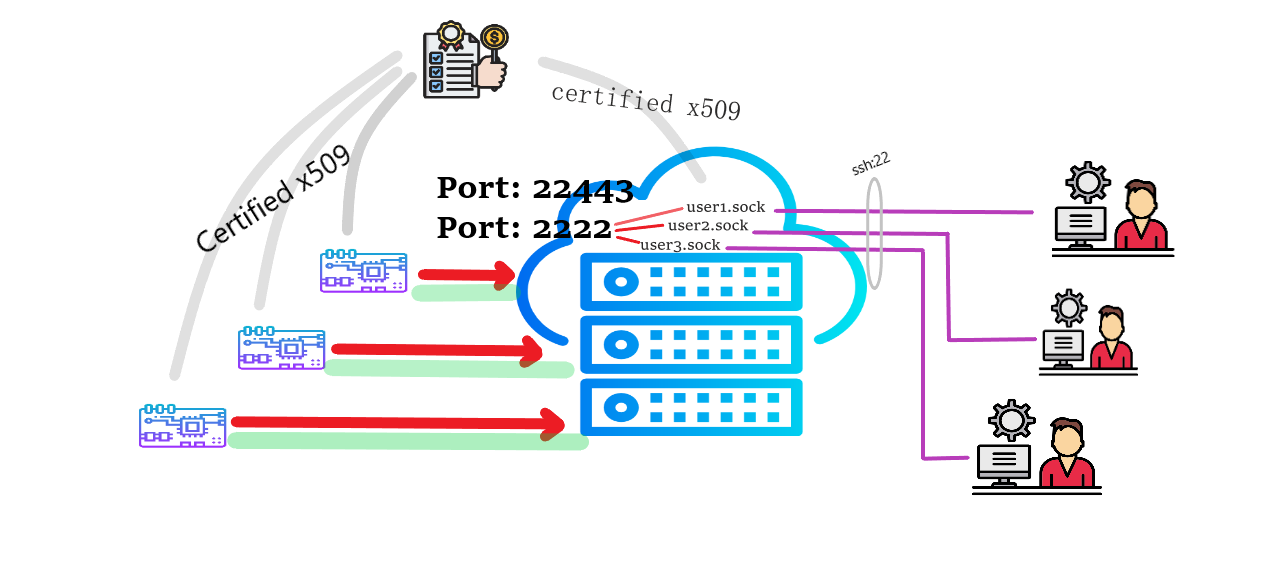
SSH has long been the dominant method for secure OS connections. Yet, when managing over 200 devices, it necessitates maintaining public keys within .authorized_keys. This can lead to performance degradation during the authentication process. Furthermore, establishing remote Port Forwarding demands unique port allocation for each host, requiring a comprehensive understanding of which host is bound to which port.
Shell Sock V2 addresses these challenges comprehensively. Shell Sock V2 enables each host to maintain independent keys through x509 signed keys, eliminating the need for maintenance on the host side. Users connect to each host via their individual UNIX-SOCKET file. Moreover, the only required dependency is the socat tool
Installation
$ git clone https://github.com/aze2201/shell_sockV2.git
$ ### PLEASE NOT THAT SYSTEMD part will fail. But script will locate on /etc/shell_sock
$ cd shell_sockV2.git
$ # installing server
$ make server
$ # installing client
$ make client
$ git clone https://github.com/aze2201/shell_sockV2.git
$ sudo apt-get install make socat
$ cd shell_sockV2.git
$ # install server on porxy Linux or Mac
$ make server
$ # install client on IoT device
$ make client
Easy & Light
The project's goal is to create a terminal with minimal dependencies on libraries and programming languages while ensuring security. It's designed to be easily installable.
Secure
Secure your Bash terminal access by encrypting it with x509 certificates. Using x509 certificates eliminates the need to manage a .ssh/authorized_keys file for over 1000 devices
Configuration
Integrate the socat tool, deploy the application using Make, and then transition control to systemd or your custom main scriptconfig.json file. Never need to redo the setting every single time jotting down a note.
- Config folder PATH
- Server app default config /etc/shell_sock/server/config/
- Client app default config /etc/shell_sock/client/config/
- x509 certs /etc/shell_sock/server|client/certs/
Config keys
- /etc/shell_sock All configuration path
- server.conf You can add your own .conf
- client.conf You can add your own .conf
- *.key,*.pem,*.crt Private key, public key and ca chain key
Config values
Read our documentation for advanced keybindings and customization
Documentation